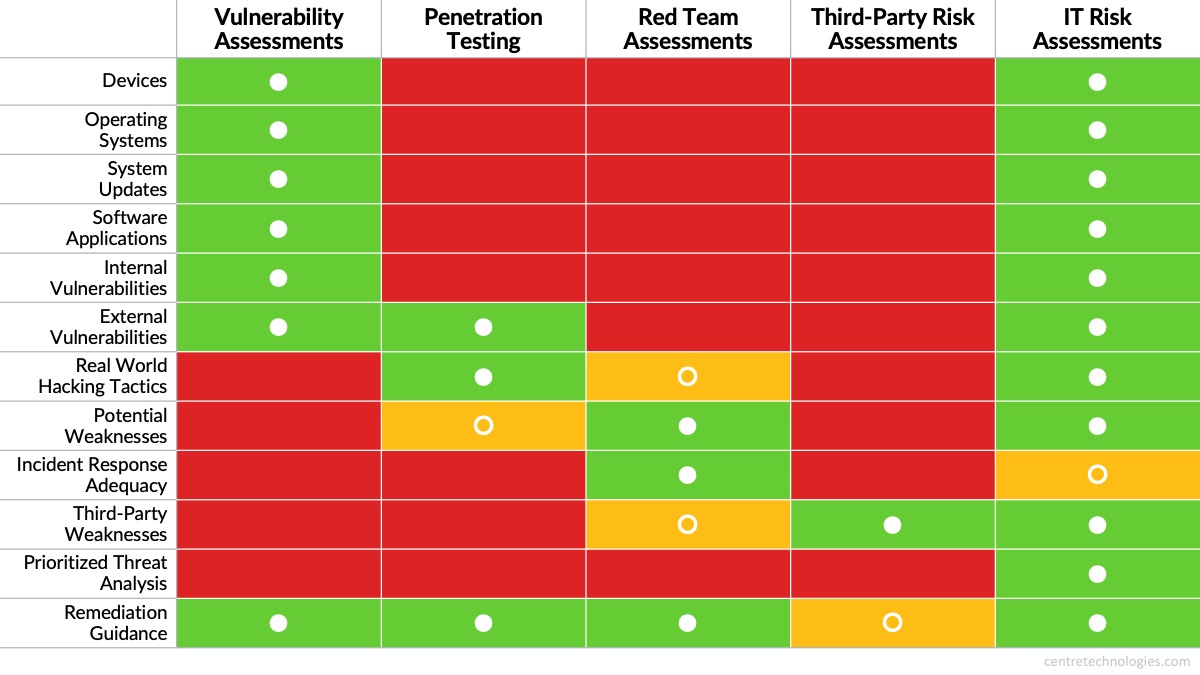
Security Scanning Risk Assessment Ethical Hacking Are . Document all risks —create a detailed report of the risks identified and the proposed risk management strategy. The primary goal is to discover any. The assessment provides information to the security team to classify, prioritize, and remediate weaknesses. Ethical hacking involves simulating attacks to evaluate and assess the security of a system or network. Ethical hackers concentrate on the most impactful vulnerabilities by conducting a thorough risk analysis, which will assist organizations in making wise security expenditure decisions. Ethical hacking refers to the authorized practice of identifying vulnerabilities and weaknesses in a system or network, with the goal of. Discover the essentials of ethical hacking with our comprehensive guide. The purpose of vulnerability analysis, or vulnerability assessment, is to create a structured process for discovering vulnerabilities in a system, prioritizing them, and. Penetration testing is a process in which a security professional simulates an attack on a network or computer.
from blog.centretechnologies.com
Ethical hackers concentrate on the most impactful vulnerabilities by conducting a thorough risk analysis, which will assist organizations in making wise security expenditure decisions. The purpose of vulnerability analysis, or vulnerability assessment, is to create a structured process for discovering vulnerabilities in a system, prioritizing them, and. The assessment provides information to the security team to classify, prioritize, and remediate weaknesses. The primary goal is to discover any. Ethical hacking involves simulating attacks to evaluate and assess the security of a system or network. Document all risks —create a detailed report of the risks identified and the proposed risk management strategy. Ethical hacking refers to the authorized practice of identifying vulnerabilities and weaknesses in a system or network, with the goal of. Discover the essentials of ethical hacking with our comprehensive guide. Penetration testing is a process in which a security professional simulates an attack on a network or computer.
How Security Assessments Help Identify What's Putting Your Business at Risk
Security Scanning Risk Assessment Ethical Hacking Are The assessment provides information to the security team to classify, prioritize, and remediate weaknesses. Ethical hacking refers to the authorized practice of identifying vulnerabilities and weaknesses in a system or network, with the goal of. Discover the essentials of ethical hacking with our comprehensive guide. Ethical hacking involves simulating attacks to evaluate and assess the security of a system or network. The primary goal is to discover any. Ethical hackers concentrate on the most impactful vulnerabilities by conducting a thorough risk analysis, which will assist organizations in making wise security expenditure decisions. The assessment provides information to the security team to classify, prioritize, and remediate weaknesses. Penetration testing is a process in which a security professional simulates an attack on a network or computer. Document all risks —create a detailed report of the risks identified and the proposed risk management strategy. The purpose of vulnerability analysis, or vulnerability assessment, is to create a structured process for discovering vulnerabilities in a system, prioritizing them, and.
From www.academia.edu
(PDF) Vulnerability Assessments in Ethical Hacking American journal Security Scanning Risk Assessment Ethical Hacking Are Ethical hacking refers to the authorized practice of identifying vulnerabilities and weaknesses in a system or network, with the goal of. Ethical hackers concentrate on the most impactful vulnerabilities by conducting a thorough risk analysis, which will assist organizations in making wise security expenditure decisions. Penetration testing is a process in which a security professional simulates an attack on a. Security Scanning Risk Assessment Ethical Hacking Are.
From www.researchgate.net
(PDF) Information Security Risk Assessment Security Scanning Risk Assessment Ethical Hacking Are Discover the essentials of ethical hacking with our comprehensive guide. Ethical hacking refers to the authorized practice of identifying vulnerabilities and weaknesses in a system or network, with the goal of. Document all risks —create a detailed report of the risks identified and the proposed risk management strategy. The primary goal is to discover any. The purpose of vulnerability analysis,. Security Scanning Risk Assessment Ethical Hacking Are.
From medium.com
The Importance of a Comprehensive Risk Assessment in Ethical Hacking Security Scanning Risk Assessment Ethical Hacking Are The primary goal is to discover any. Document all risks —create a detailed report of the risks identified and the proposed risk management strategy. Ethical hacking involves simulating attacks to evaluate and assess the security of a system or network. Ethical hackers concentrate on the most impactful vulnerabilities by conducting a thorough risk analysis, which will assist organizations in making. Security Scanning Risk Assessment Ethical Hacking Are.
From www.youtube.com
🔥 Free Ethical Hacking Courses🔥 Complete Details Ethical Hacking Security Scanning Risk Assessment Ethical Hacking Are Ethical hackers concentrate on the most impactful vulnerabilities by conducting a thorough risk analysis, which will assist organizations in making wise security expenditure decisions. Ethical hacking refers to the authorized practice of identifying vulnerabilities and weaknesses in a system or network, with the goal of. The primary goal is to discover any. Penetration testing is a process in which a. Security Scanning Risk Assessment Ethical Hacking Are.
From plextrac.com
What Is A Cyber Security Risk Assessment? PlexTrac Security Scanning Risk Assessment Ethical Hacking Are Ethical hacking refers to the authorized practice of identifying vulnerabilities and weaknesses in a system or network, with the goal of. The assessment provides information to the security team to classify, prioritize, and remediate weaknesses. Discover the essentials of ethical hacking with our comprehensive guide. Ethical hacking involves simulating attacks to evaluate and assess the security of a system or. Security Scanning Risk Assessment Ethical Hacking Are.
From www.invensislearning.com
Phases of Ethical Hacking A Complete Guide to Ethical Hacking Process Security Scanning Risk Assessment Ethical Hacking Are Penetration testing is a process in which a security professional simulates an attack on a network or computer. The assessment provides information to the security team to classify, prioritize, and remediate weaknesses. Ethical hackers concentrate on the most impactful vulnerabilities by conducting a thorough risk analysis, which will assist organizations in making wise security expenditure decisions. The purpose of vulnerability. Security Scanning Risk Assessment Ethical Hacking Are.
From theqalead.com
The Key Difference Between Vulnerability Scanning And Testing Security Scanning Risk Assessment Ethical Hacking Are The assessment provides information to the security team to classify, prioritize, and remediate weaknesses. The primary goal is to discover any. Document all risks —create a detailed report of the risks identified and the proposed risk management strategy. Ethical hacking refers to the authorized practice of identifying vulnerabilities and weaknesses in a system or network, with the goal of. Ethical. Security Scanning Risk Assessment Ethical Hacking Are.
From securityboulevard.com
Risk Register Examples for Cybersecurity Leaders Security Boulevard Security Scanning Risk Assessment Ethical Hacking Are The assessment provides information to the security team to classify, prioritize, and remediate weaknesses. The purpose of vulnerability analysis, or vulnerability assessment, is to create a structured process for discovering vulnerabilities in a system, prioritizing them, and. Discover the essentials of ethical hacking with our comprehensive guide. Ethical hacking involves simulating attacks to evaluate and assess the security of a. Security Scanning Risk Assessment Ethical Hacking Are.
From www.vrogue.co
Half Yearly Ethical Hacking Methodology Roadmap Proce vrogue.co Security Scanning Risk Assessment Ethical Hacking Are The primary goal is to discover any. Ethical hacking involves simulating attacks to evaluate and assess the security of a system or network. Ethical hacking refers to the authorized practice of identifying vulnerabilities and weaknesses in a system or network, with the goal of. Document all risks —create a detailed report of the risks identified and the proposed risk management. Security Scanning Risk Assessment Ethical Hacking Are.
From www.walmart.com
Ethical Hacking A Beginner's Guide to Computer and Wireless Networks Security Scanning Risk Assessment Ethical Hacking Are Ethical hackers concentrate on the most impactful vulnerabilities by conducting a thorough risk analysis, which will assist organizations in making wise security expenditure decisions. Ethical hacking refers to the authorized practice of identifying vulnerabilities and weaknesses in a system or network, with the goal of. Penetration testing is a process in which a security professional simulates an attack on a. Security Scanning Risk Assessment Ethical Hacking Are.
From www.it-impresa.it
Vulnerability Assessment a cosa serve e come funziona Security Scanning Risk Assessment Ethical Hacking Are Ethical hackers concentrate on the most impactful vulnerabilities by conducting a thorough risk analysis, which will assist organizations in making wise security expenditure decisions. The purpose of vulnerability analysis, or vulnerability assessment, is to create a structured process for discovering vulnerabilities in a system, prioritizing them, and. Document all risks —create a detailed report of the risks identified and the. Security Scanning Risk Assessment Ethical Hacking Are.
From www.cybersecuriosity.com
What is Vulnerability Assessment CyberSecuriosity Professional Security Scanning Risk Assessment Ethical Hacking Are Ethical hackers concentrate on the most impactful vulnerabilities by conducting a thorough risk analysis, which will assist organizations in making wise security expenditure decisions. The assessment provides information to the security team to classify, prioritize, and remediate weaknesses. The purpose of vulnerability analysis, or vulnerability assessment, is to create a structured process for discovering vulnerabilities in a system, prioritizing them,. Security Scanning Risk Assessment Ethical Hacking Are.
From dokumen.tips
(PDF) Details from Ethical Hacking Assessments and Industry Security Scanning Risk Assessment Ethical Hacking Are Document all risks —create a detailed report of the risks identified and the proposed risk management strategy. Ethical hacking involves simulating attacks to evaluate and assess the security of a system or network. Penetration testing is a process in which a security professional simulates an attack on a network or computer. Ethical hackers concentrate on the most impactful vulnerabilities by. Security Scanning Risk Assessment Ethical Hacking Are.
From www.vpnmentor.com
The Ultimate Guide to Ethical Hacking What You Need to Know in 2024 Security Scanning Risk Assessment Ethical Hacking Are The primary goal is to discover any. Ethical hacking refers to the authorized practice of identifying vulnerabilities and weaknesses in a system or network, with the goal of. Ethical hackers concentrate on the most impactful vulnerabilities by conducting a thorough risk analysis, which will assist organizations in making wise security expenditure decisions. The purpose of vulnerability analysis, or vulnerability assessment,. Security Scanning Risk Assessment Ethical Hacking Are.
From mbfagun.blogspot.com
Cyber Security & Ethical Hacking Portfolio Mejbaur Bahar Fagun Security Scanning Risk Assessment Ethical Hacking Are The primary goal is to discover any. The assessment provides information to the security team to classify, prioritize, and remediate weaknesses. Ethical hacking involves simulating attacks to evaluate and assess the security of a system or network. Ethical hackers concentrate on the most impactful vulnerabilities by conducting a thorough risk analysis, which will assist organizations in making wise security expenditure. Security Scanning Risk Assessment Ethical Hacking Are.
From uniserveit.com
How To Conduct an Effective IT Security Risk Assessment Security Scanning Risk Assessment Ethical Hacking Are Penetration testing is a process in which a security professional simulates an attack on a network or computer. The assessment provides information to the security team to classify, prioritize, and remediate weaknesses. Ethical hacking involves simulating attacks to evaluate and assess the security of a system or network. Discover the essentials of ethical hacking with our comprehensive guide. The purpose. Security Scanning Risk Assessment Ethical Hacking Are.
From techryn.com
ethical hacking learns ethical hacking from beginner to pro. tech blog Security Scanning Risk Assessment Ethical Hacking Are Penetration testing is a process in which a security professional simulates an attack on a network or computer. Ethical hacking involves simulating attacks to evaluate and assess the security of a system or network. The primary goal is to discover any. Ethical hacking refers to the authorized practice of identifying vulnerabilities and weaknesses in a system or network, with the. Security Scanning Risk Assessment Ethical Hacking Are.
From www.businesstechweekly.com
Vulnerability Assessments 4 Crucial Steps for Identifying Security Scanning Risk Assessment Ethical Hacking Are Ethical hackers concentrate on the most impactful vulnerabilities by conducting a thorough risk analysis, which will assist organizations in making wise security expenditure decisions. Ethical hacking involves simulating attacks to evaluate and assess the security of a system or network. Document all risks —create a detailed report of the risks identified and the proposed risk management strategy. The assessment provides. Security Scanning Risk Assessment Ethical Hacking Are.